Remote Interviews , Remote Staffing
Do’s and Don’ts for remote interviews for software developers
Dressing up for an interview and traveling with a folder with your resume and accolades...
The world has changed with the outbreak of COVID-19, and the way we work is no exception. The outbreak has led to a sudden boom in remote working worldwide with organizations moving their workforce to their homes. With no face-to-face interactions, it is only natural for employees to feel isolated and lose a sense of belongingness towards their organization. And in case you are wondering, yes, it is a big concern!
But there is another growing concern that all organizations should be worried about – remote cyber security issues. According to a recent study by Proofpoint, hackers are sending 26% more malware than they were before the pandemic started. This means that hackers are on the prowl and looking for vulnerabilities to exploit.

With so many employees working remotely, organizations must take extra steps to ensure they don’t become victims of cyberattacks or fraud. As businesses begin to return to normalcy, it will be important for organizations to implement new processes and policies that address current security issues.
Remote working has been on the rise since the world was hit by a pandemic. Remote cyber security threats are on the rise for businesses and organizations, especially for those who have recently transitioned to a remote working environment, the pandemic created an unprecedented level of cyber threat activity. According to recent reports by Gartner, 82% of companies plan to allow their employees to work remotely at least part of the time, even after COVID-19 is no longer a threat.
Remote work may not be going away anytime soon. According to a recent study, nearly four in ten workers will continue to work remotely, even after the pandemic is over. This is great news for businesses. Remote work helps them lower their operational costs by eliminating the need for large offices and opens the door to hiring remote employees from all over the world. The bad news is that remote work comes with some serious cyber security risks.
With employees working outside of the office, it’s much harder for businesses to ensure that their data is protected from cyber criminals and other threats. This makes them more vulnerable to attacks like data breaches, ransomware, social engineering attacks, and more.
You may not be aware of the fact that in January 2021, global cybercrime damages were estimated at $6 trillion annually by analysts and researchers. This includes damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, and fraud.
With most employees working from home, enterprise networks are more vulnerable than ever before. Companies must safeguard their employees’ devices, as well as their home networks from potential cyber threats.
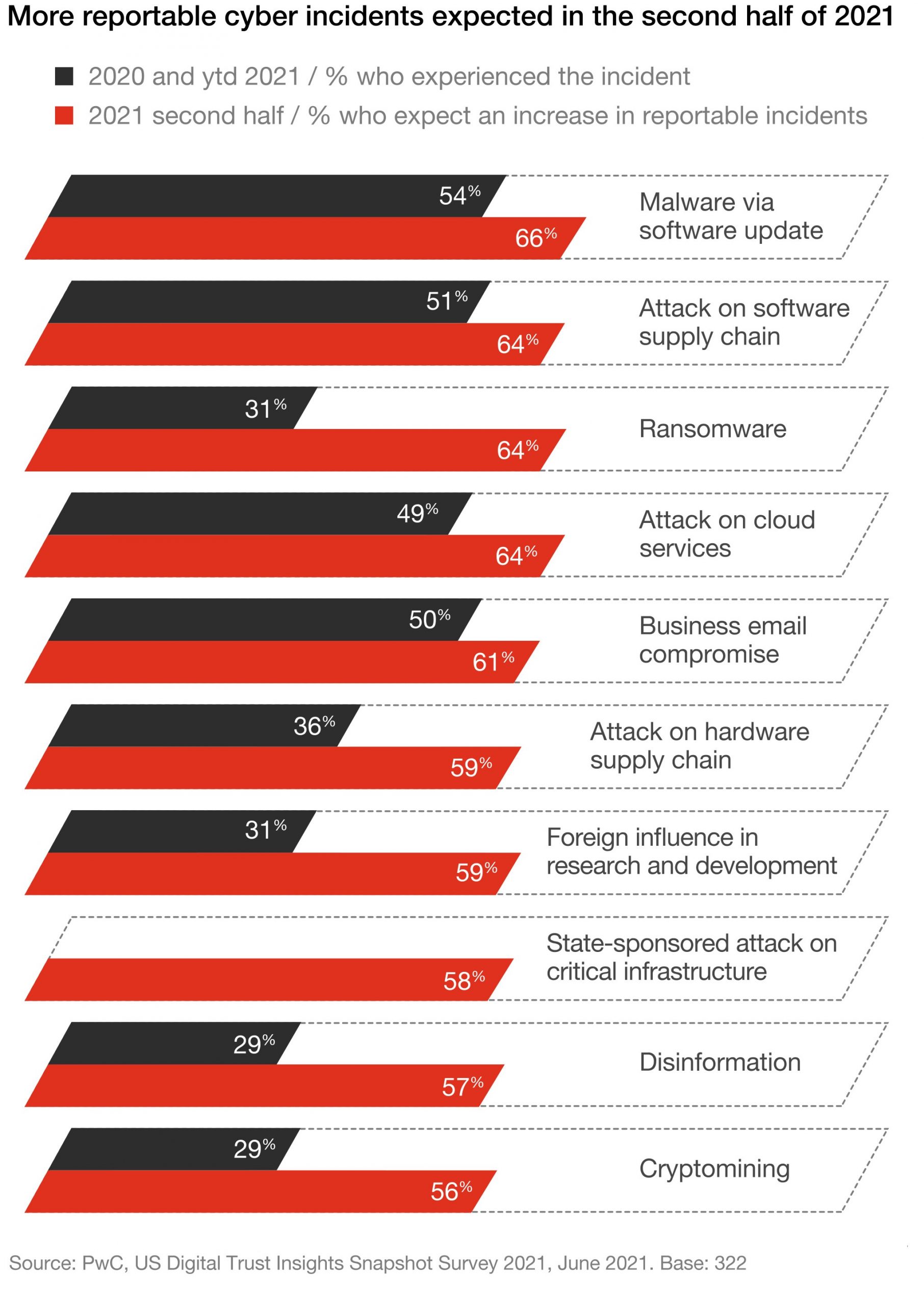
The sudden shift to remote working during the pandemic is a primary reason for cybercrime growth. According to a survey by PwC, the percentage of organizations that said they had been targeted by a malware cyberattack via software update increased by (54%), attacks on software supply chain increased by (51%) and attack on business through email compromise increased by (50%).
While remote working has become a popular trend in the past few months, companies need to consider the security measures and best practices that need to be followed to keep their remote workers’ data safe from potential cyber threats.
As cyber attacks continue to increase across the globe, there are a few key points companies must consider while working on setting up a secure remote work environment for their employees:
1. Implement a Company-Wide Cyber security Policy
The first step in helping your remote employees is by implementing a company-wide cybersecurity policy for all users. This policy should be clear and concise so that all of your employees can follow it easily.
Organizations must ensure that all of their remote workers follow basic security protocols such as not clicking on suspicious links, updating passwords regularly, and installing antivirus software on their devices.
It should include requirements like what types of websites they can visit, what types of downloads are allowed, and what types of files they should avoid sharing. It should also outline what types of behaviors will result in termination and explain how to report breaches or suspicious activity.
2. Cloud access:
Cybercriminals also target your cloud infrastructure and applications as they are aware that businesses store most of their data in the cloud.
Cloud access is often the weakest link in an organization’s security chain. It’s critical to ensure that your cloud services are secure and that only the right people have access to them. This can be done by implementing role-based access control and auditing user behavior regularly.
To prevent this from happening, you should implement a cloud access security broker (CASB) solution that provides complete visibility into all the activities taking place in your cloud environment. This will help you monitor any suspicious activity or access confidential data in real-time.
You should ensure that your customers’ data is securely stored by using Google Cloud Platform or Microsoft Azure, which helps safeguard against unauthorized access and malicious activity. These platforms also secure data with encryption while it’s at rest and in transit, including encrypting data stored on disk at the block level, and encrypting all network traffic between the customer’s virtual machine (VM) instances, as well as between VMs and other services within Google’s network.
The use of cloud drives should be encouraged to ensure that critical information is stored safely and can only be accessed by authorized personnel. All remote workers should formulate a proper cloud storage strategy based on their needs and preferences.
You should also limit what users can do within a service such as Google Drive or Dropbox so they don’t accidentally expose sensitive information.
3. VPNs:
A VPN or Virtual Private Network is an encrypted connection between your computer and the VPN server. It helps you stay safe on public Wi-Fi and allows you to browse the internet anonymously by adding a layer of security between you and the server you’re accessing through “tunneling” your data. It also ensures that if anyone tries to intercept your traffic, it would be useless as it would be encrypted.
A VPN can help prevent hackers from getting access to sensitive company information by making sure no one can snoop on your network traffic. Virtual Private Networks (VPNs) have become an essential tool for businesses of all sizes because they ensure that their connection will be secure and fully encrypted at all times. Since all of your employees will be working remotely, they must use virtual private network (VPN) software.
A virtual private network (VPN) creates an encrypted link between the user’s device and your network, making it harder for hackers to obtain sensitive information or infect devices with malware. It’s important to ensure that all of your employees are using a VPN when accessing company data remotely.
When using a VPN service, it is important to ensure that it does not store logs of user activity or personal data, such as names and payment information.
4. Focus on Cybersecurity Training:
Cybersecurity training is a must for all employees, but especially for remote workers, who may be more prone to phishing attacks or malware downloads. Ensure that your employees have updated knowledge about current cyber threats and know how to identify and report any suspicious activity.
You must educate your remote employees about potential cyber risks and how they can prevent them. This includes ensuring that they use only secure Wi-Fi networks and don’t download files or click links from unknown sources.
5. Deploy Endpoint Security Solutions for All Employees’ Devices
Endpoints are devices that can connect to the corporate network, such as laptops, desktops, and mobile phones. They are considered the most vulnerable target for cybercriminals. Businesses should implement endpoint security solutions to secure their remote workforce. These solutions provide patch management and vulnerability detection to ensure all your employees’ devices are updated with the latest patches and software.
As people rely more on their devices for work, you may be tempted to cut corners when it comes to security. However, this could leave your business at risk if you’re not careful about what you do and don’t allow it on employee devices and networks.
Endpoint protection is vital when it comes to securing your network against potential threats. Invest in good endpoint protection software that allows you to control what your remote employees are doing on their devices at all times. The software should provide real-time monitoring and reporting of any suspicious activity across apps, files, and programs used by your employees on their devices.
6. Install Security Software on Devices
Never assume that someone else is responsible for managing cybersecurity within your organization. Ensure that you install robust antivirus software on all devices used by your employees while working remotely. Install antivirus software on all employee devices – Cybercriminals often use malware to gain unauthorized access to networks, devices, and data. Antivirus software helps protect against this threat by scanning.
You should install antivirus software on all employee devices, whether it’s a smartphone, tablet, or laptop. devices for malicious programs and removing them before they can cause any damage. This helps prevent malware from entering your systems through employee devices.
Some examples include Avast, Bitdefender, ESET, McAfee, NortonLifeLock, and Webroot. These are effective in detecting and removing malware and viruses remotely via an internet connection. Ensure that all software is updated regularly – As soon as a security flaw is discovered, developers will release an update that patches the hole. To protect against potential vulnerabilities, you need to ensure that all software is updated regularly. This can be done automatically on many systems.
7. Multi-factor authentication:
Multi-factor authentication (MFA) is another crucial cybersecurity solution for remote work environments because it requires users to verify their identity using two or more credentials before accessing any device or application connected to the network.
Using MFA solutions ensure that only authorized users have access to your organization’s data and systems, which prevents unauthorized parties from using stolen passwords to breach your network.
The current global pandemic has changed the way businesses work. Most companies have now moved to remote working cultures, but how safe is their data? Remote cyber security breaches are on the rise and hackers are finding new ways to attack individual devices and systems. This means more data is being exposed to potential threats.
While a lot of organizations have a personal firewall and antivirus software installed on their employees’ computers, laptops, and smartphones, it’s not enough to protect them from cyber-attacks. More needs to be done at an organizational level to keep employee data safe. Companies need to take certain steps to safeguard their sensitive data from cyber-attacks.
BorderlessMind has helped many companies and startups hire their remote cyber security team and set up a secure remote work environment for their employees. If you’re looking to set up a secure remote working environment with your employees, contact our talent experts to hire remote cyber security team for your business today!

Dressing up for an interview and traveling with a folder with your resume and accolades...

In the ever-evolving world of technology, Java continues to be a popular and widely used...

Remote work has been around for a while, but the COVID-19 pandemic accelerated its adoption....

Introduction: Case 1: In 2016, Ravi was a college dropout, and his decision to drop...

While degree-based hiring has been the traditional approach, the latest trend in IT recruitment is...

As per Glassdoor Data Engineering ranked in the top 15 of “50 Best Jobs in...

Global advances in technology are increasing the demand for skilled IT professionals at an exponential...

As the trend towards a remote working setup continues to grow, managing such teams has...

Outsourcing IT services has become increasingly popular among companies and business owners looking to expand...